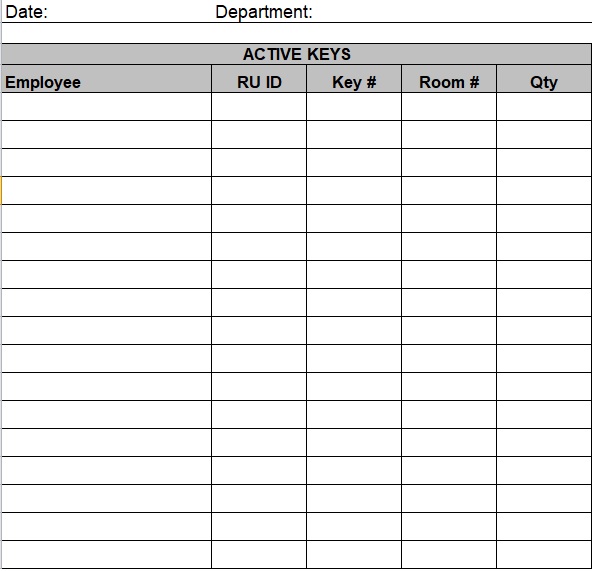
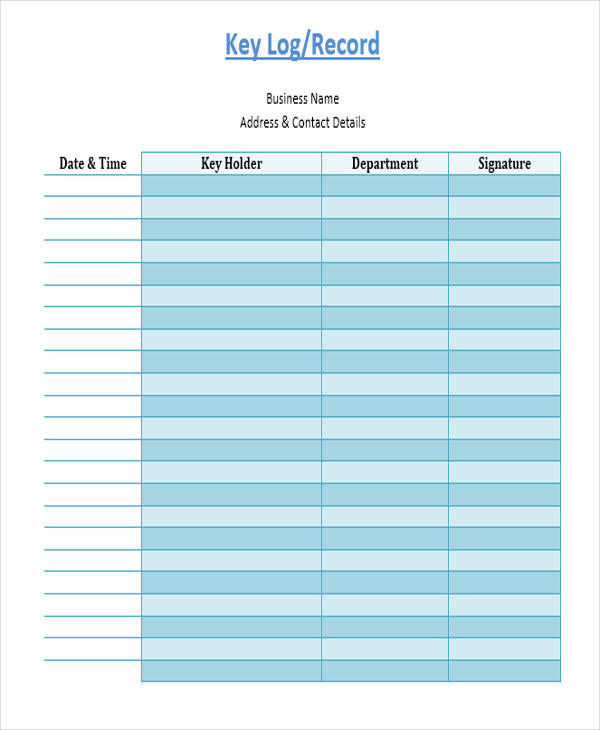
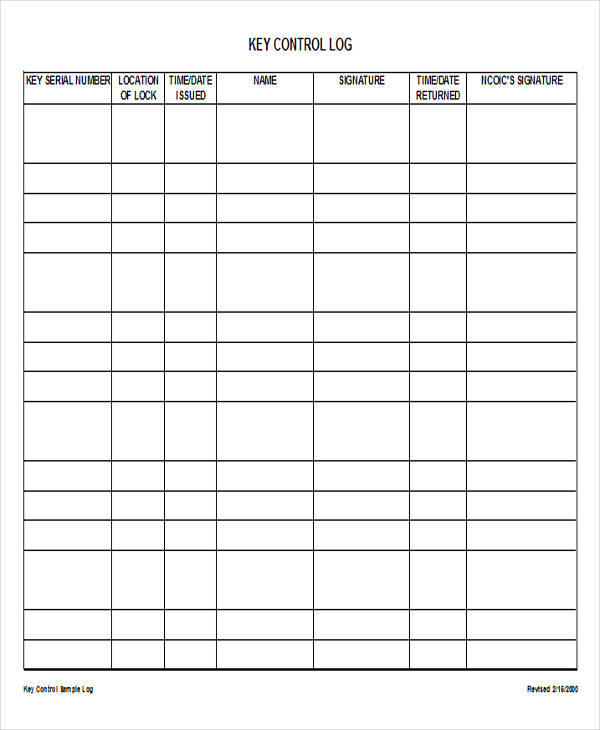
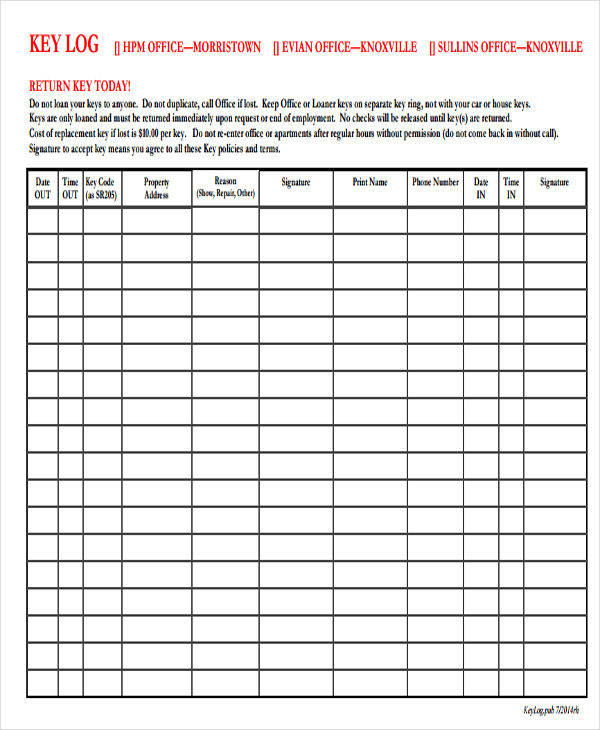
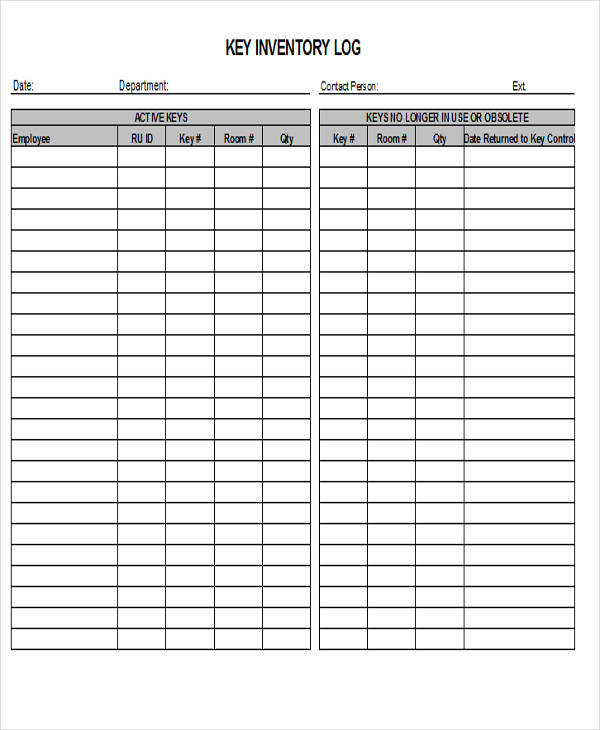
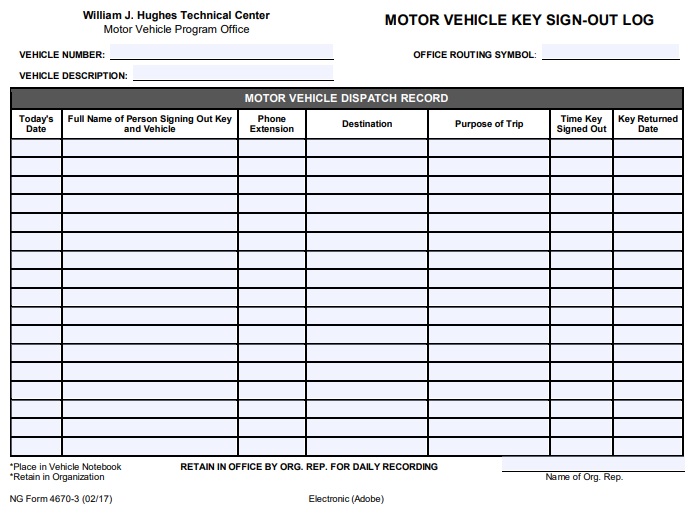
Edit your key log sheet online. This log enhances security measures, helps in identifying any unauthorized access, and ensures accountability for the distribution and usage of keys within a specified environment. Type text, add images, blackout confidential details, add comments, highlights and more. The log captures details such as key or device identifiers, recipients, dates of issuance and return, and any relevant notes or observations. View our free and editable key logging templates for excel or google sheets.
This intuitive tool simplifies tracking and organizing keys effortlessly. If you need to create a key log to keep track of key issuances and returns, and other necessary information, our available selection of samples and templates will be useful in formatting and creating your key log. These key logging spreadsheet templates are easy to modify and you can customize the design, the header, table, formulas to suit your needs. Download now to finish your work in minutes. The log captures details such as key or device identifiers, recipients, dates of issuance and return, and any relevant notes or observations.
Set alerts for replacement or reordering, monitor usage, and streamline access. The log captures details such as key or device identifiers, recipients, dates of issuance and return, and any relevant notes or observations. This intuitive tool simplifies tracking and organizing keys effortlessly. The key log is designed to keep a comprehensive record of access to secured areas by documenting who has been issued keys and when. These key logging spreadsheet templates are easy to modify and you can customize the design, the header, table, formulas to suit your needs.
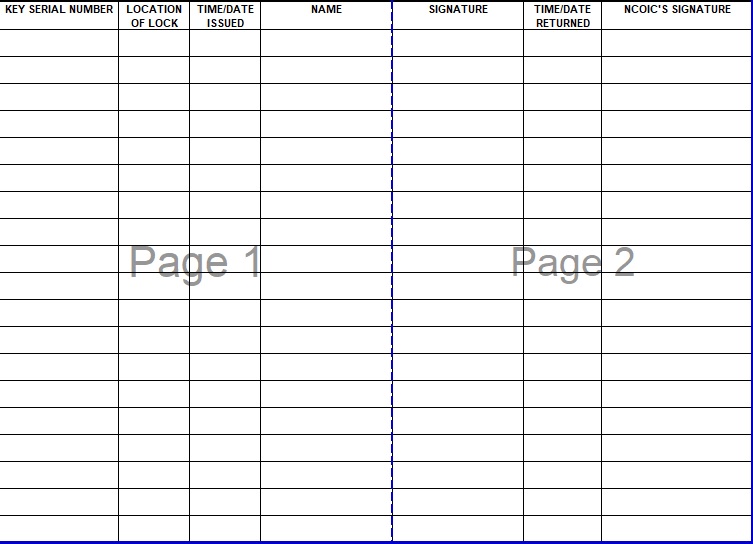
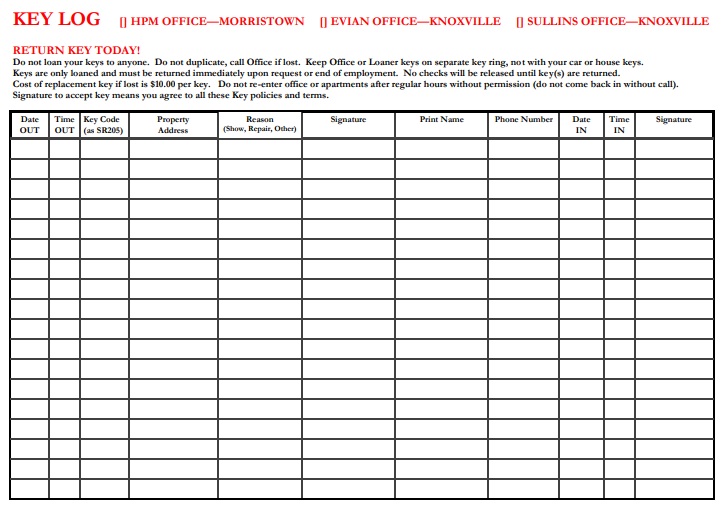
Send key log template excel via email, link, or fax. This intuitive tool simplifies tracking and organizing keys effortlessly. These key logging spreadsheet templates are easy to modify and you can customize the design, the header, table, formulas to suit your needs. This log enhances security measures, helps in identifying any unauthorized access, and ensures accountability for the distribution and usage of keys within a specified environment. Download now to finish your work in minutes. The key log is designed to keep a comprehensive record of access to secured areas by documenting who has been issued keys and when. Physical plant's key control policy 05.120 requires department heads (usually through a designated key control person) to track and document all key issuances, returns, custody transfers, and lost, stolen or unreturned keys within the department, and to provide a copy of the departments key tracking log to locksmith services. It helps maintain security, monitor key access, and ensure accountability for keyholders. This log aids in tracking key movements, identifying authorized personnel, and detecting any. The log captures details such as key or device identifiers, recipients, dates of issuance and return, and any relevant notes or observations. Unlock seamless management with our key inventory template! If you need to create a key log to keep track of key issuances and returns, and other necessary information, our available selection of samples and templates will be useful in formatting and creating your key log. Type text, add images, blackout confidential details, add comments, highlights and more. You can also download it, export it or print it out. View our free and editable key logging templates for excel or google sheets.
The Log Captures Details Such As Key Or Device Identifiers, Recipients, Dates Of Issuance And Return, And Any Relevant Notes Or Observations.
Most importantly, it provides you simplest way of making your document. Physical plant's key control policy 05.120 requires department heads (usually through a designated key control person) to track and document all key issuances, returns, custody transfers, and lost, stolen or unreturned keys within the department, and to provide a copy of the departments key tracking log to locksmith services. Set alerts for replacement or reordering, monitor usage, and streamline access. Download now to finish your work in minutes.
Edit Your Key Log Sheet Online.
You can also download it, export it or print it out. This intuitive tool simplifies tracking and organizing keys effortlessly. Unlock seamless management with our key inventory template! If you need to create a key log to keep track of key issuances and returns, and other necessary information, our available selection of samples and templates will be useful in formatting and creating your key log.
It Helps Maintain Security, Monitor Key Access, And Ensure Accountability For Keyholders.
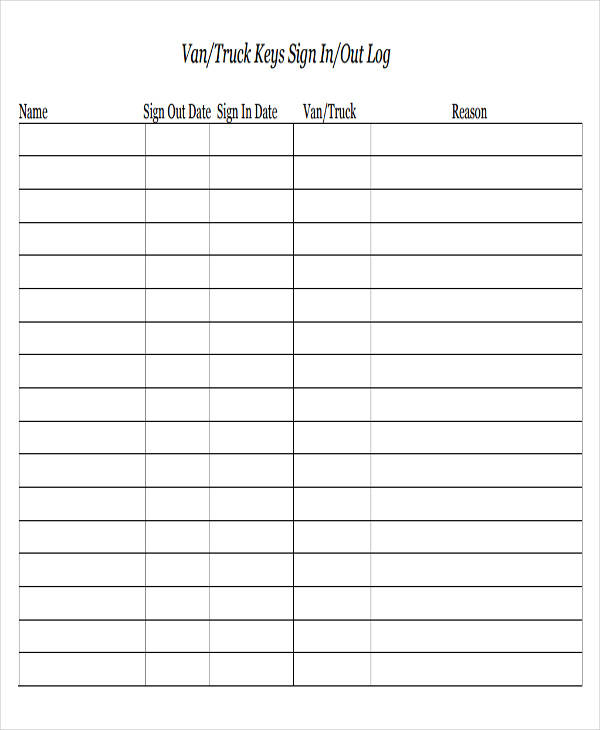
This log aids in tracking key movements, identifying authorized personnel, and detecting any. The master key log is maintained to monitor the issuance, usage, and return of master keys, ensuring security and accountability for access to designated areas. These key logging spreadsheet templates are easy to modify and you can customize the design, the header, table, formulas to suit your needs. View our free and editable key logging templates for excel or google sheets.
This Log Enhances Security Measures, Helps In Identifying Any Unauthorized Access, And Ensures Accountability For The Distribution And Usage Of Keys Within A Specified Environment.
Type text, add images, blackout confidential details, add comments, highlights and more. The key log is designed to keep a comprehensive record of access to secured areas by documenting who has been issued keys and when. Send key log template excel via email, link, or fax. Sign it in a few clicks.